Enhance Your Data Protection With Premier Cloud Storage Space Provider
In a period where data protection is paramount, leveraging premier cloud storage services can be a tactical action for guarding your company's important information. By checking out the comprehensive features and advantages of premier cloud storage services, organizations can proactively boost their information protection strategies and remain in advance of possible dangers in a significantly digital landscape.
Advantages of Cloud Storage Solutions
Cloud storage solutions offer unrivaled comfort and scalability for organizations and individuals looking for safe and secure data protection services. One of the primary advantages is the flexibility they provide in accessing information from anywhere with a net link. This accessibility eliminates the demand for physical storage space tools, decreasing the threat of data loss due to equipment failures or theft. Furthermore, cloud storage solutions commonly use automated backup features, making certain that information is regularly saved and shielded without the need for hands-on treatment.
An additional substantial advantage is the scalability of cloud storage solutions. Users can conveniently update their storage ability as their requirements expand, without the demand of purchasing additional hardware. This scalability is especially useful for businesses experiencing quick growth or ever-changing storage space demands.
Moreover, cloud storage space solutions generally supply cost-effective remedies contrasted to typical information storage space methods. Users can spend for the precise amount of storage they require, avoiding unneeded expenditures on unused room. Generally, the benefits of cloud storage space solutions make them a useful asset for people and services looking to improve their data security methods.
Advanced Protection Functions
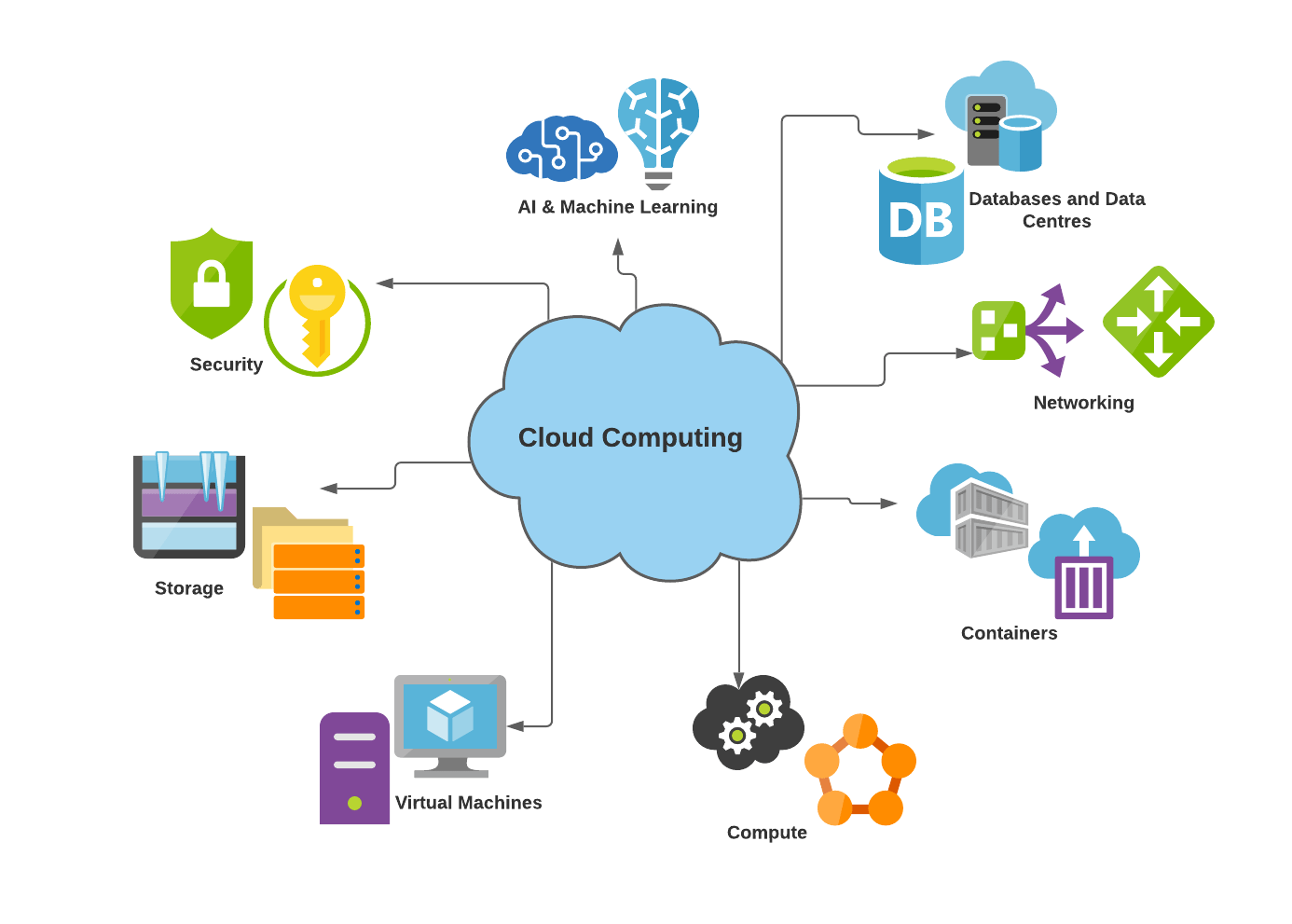
In addition, leading cloud storage solutions employ breach discovery and avoidance systems to continually keep an eye on for any type of suspicious tasks within the storage environment. This aggressive technique assists in reducing and identifying security breaches in real-time. Regular safety audits and susceptability evaluations are performed to make certain that the system meets the current safety and security standards and techniques.
Additionally, role-based accessibility controls are made use of to restrict information access based on certain individual duties and duties, lowering the risk of unapproved information direct exposure - cloud services press release. By integrating these advanced security features, premier cloud storage space solutions supply a protected setting for storing and handling sensitive data, offering individuals assurance concerning their data security requires
Information Encryption and Compliance
Making use of robust security procedures and sticking to rigid regulative requirements, top cloud storage solutions make sure information protection and compliance with market standards. By transforming data into complex codes that can only be accessed with the appropriate decryption key, cloud storage carriers prevent unauthorized accessibility and protect data stability.
Along with security, cloud universal cloud Service storage services ensure compliance by routinely conducting safety and security audits, maintaining thorough logs of information accessibility and modifications, and providing clear data governance practices. Conformity with market requirements not just improves data defense but also constructs trust with clients and partners. By adhering to strict encryption methods and regulative demands, top cloud storage space services provide a compliant and safe service for services seeking to shield their useful data assets.
Remote Access and Collaboration
To facilitate smooth data accessibility and collaboration, leading cloud storage solutions provide durable services for remote work atmospheres. universal cloud Service. With the capability to store and access information from anywhere with a net connection, workers can collaborate on projects in real-time, irrespective of their physical area. Cloud storage space solutions provide safe platforms for group members to share records, folders, and documents effortlessly, boosting productivity and performance within organizations
Moreover, these services frequently include attributes such as variation control, documents syncing, and authorization setups, permitting teams to work collaboratively without the threat of data duplication or unauthorized accessibility. On the whole, the remote access and cooperation capacities provided by premier cloud storage services are important for modern-day services looking to adapt to the developing nature of job atmospheres.
Catastrophe Recovery and Redundancy
Premier cloud storage space solutions focus on calamity recovery and redundancy to make sure information protection and continuity in case of unforeseen interruptions. Disaster recovery methods are important in securing information against prospective risks like natural disasters, cyberattacks, or system failures. By implementing durable calamity healing plans, cloud storage space solutions can minimize downtime and information loss, making it possible for services to return to operations swiftly.
Redundancy plays a vital function in enhancing information security by replicating information across several web servers or data centers. This redundancy makes sure that even if one web server or area falls short, data stays easily accessible from alternate sources. Additionally, cloud storage space suppliers usually utilize sophisticated technologies like information matching and automated back-ups to maintain redundancy and information honesty.
Normal testing of disaster healing plans and redundancy procedures is vital to guarantee their performance. By performing regular examinations and simulations, cloud storage space services can recognize susceptabilities and make necessary improvements to boost data protection and guarantee business connection. On the whole, focusing on catastrophe recovery and redundancy in cloud storage space services is crucial for mitigating threats and preserving data durability.
Verdict
Finally, premier cloud storage space solutions use organizations sophisticated safety attributes, information security, compliance with guidelines, remote accessibility, cooperation devices, and disaster recuperation capacities. These services provide thorough data protection and comfort for organizations aiming to boost their data security steps. By using top cloud storage services, companies can ensure the safety and security, access, and resilience of their valuable data properties in today's digital landscape.
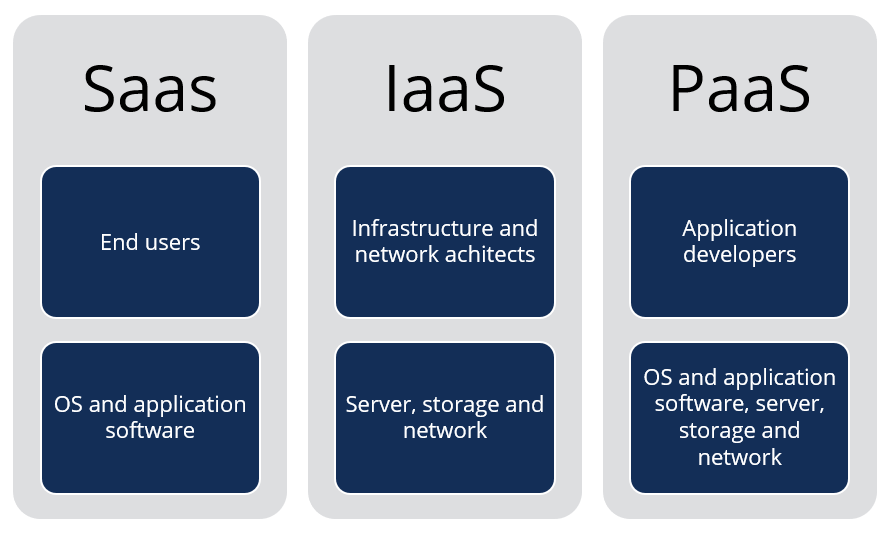
These services give detailed data protection and peace of mind for companies looking to enhance their information safety and security actions.